Understanding What Are Security Logs and Why They Matter
In the world of cybersecurity, knowing what are security logs can mean the difference between preventing a cyberattack and missing a critical warning sign. Security logs are more than just technical records—they are the digital footprints of every action, event, and change happening within your IT environment. From user logins to unauthorized access attempts, these logs provide a detailed history that helps organizations monitor, investigate, and protect their systems.
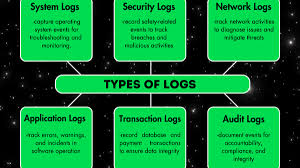
What Are Security Logs?
Security logs are specialized files generated by systems, applications, firewalls, and security devices. They capture specific events related to system access, user activity, network traffic, and security controls. These logs are crucial for detecting abnormal behavior, spotting potential threats, and meeting compliance requirements.
Types of Security Logs
1. Authentication Logs
These record successful and failed login attempts, making it easier to spot brute-force attacks or unauthorized access.
2. Firewall and Network Logs
They track incoming and outgoing network connections, including blocked or suspicious traffic.
3. System Event Logs
These document changes in configuration, file access, and operating system updates.
4. Application Security Logs
Many business applications generate logs showing user interactions and any security-related alerts.
Why Security Logs Are Important
Threat Detection and Prevention
Security logs help identify unusual activities—like multiple failed login attempts or unexpected data transfers—before they escalate into major breaches.
Compliance and Auditing
Regulations like GDPR, HIPAA, and PCI-DSS require organizations to maintain and review security logs to prove adherence to security protocols.
Incident Investigation
If a breach occurs, logs act as a forensic record, allowing security teams to track exactly what happened, when, and how.
How to Manage Security Logs Effectively
Centralized Logging
Using a Security Information and Event Management (SIEM) system allows organizations to collect logs from multiple sources into one location for easier monitoring.
Log Parsing and Analysis
Security logs can be massive and unstructured. Applying log parsing helps extract meaningful insights quickly, making threat detection faster and more accurate.
Regular Monitoring and Alerts
Automated alerts ensure that security teams are notified immediately of suspicious activity.
Best Practices for Security Log Management
- Retain logs for an appropriate period as per compliance requirements.
- Use encryption to protect log integrity.
- Schedule regular reviews and audits of log data.
- Implement role-based access to prevent tampering.
Final Thoughts
Security logs are not just an IT formality—they are a frontline defense against cyber threats. Understanding what are security logs and managing them effectively enables businesses to act faster, detect intrusions early, and maintain regulatory compliance. In an age where cyberattacks can cripple operations, proper log management isn’t optional—it’s a necessity.




